Private Cloud
Each customer instance of Thundermoth is built in a separate Virtual Private Cloud, ensuring complete data and network isolation.

Segmented Architecture
Thundermoth’s segmented software architecture follows industry best-practices for SaaS design.
Though we prefer moths, we follow all OWASP standards and security principles.
Customer Facing Protections
Thundermoth offers comprehensive customer facing security protections including multi-factor authentication (MFA), granular role-based access, access logs, operation logs, history, detailed reporting, and IP whitelisting.

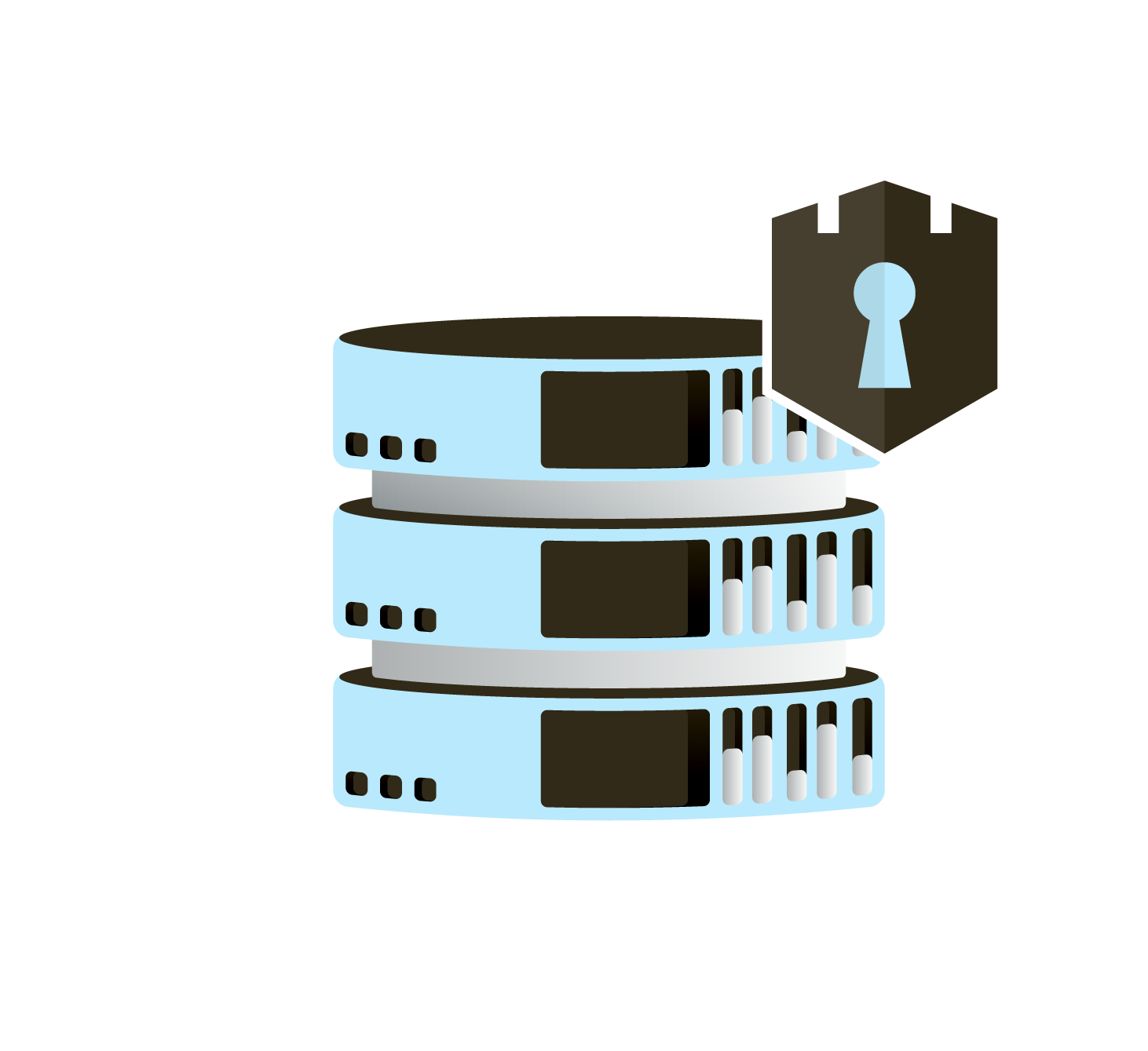
Data Security
All data is isolated, encrypted and monitored by our cloud security stack.
Data is only allowed to move from rest when the specifically allowed requests are made from the correct source and using the correct secure protocols and credentials.
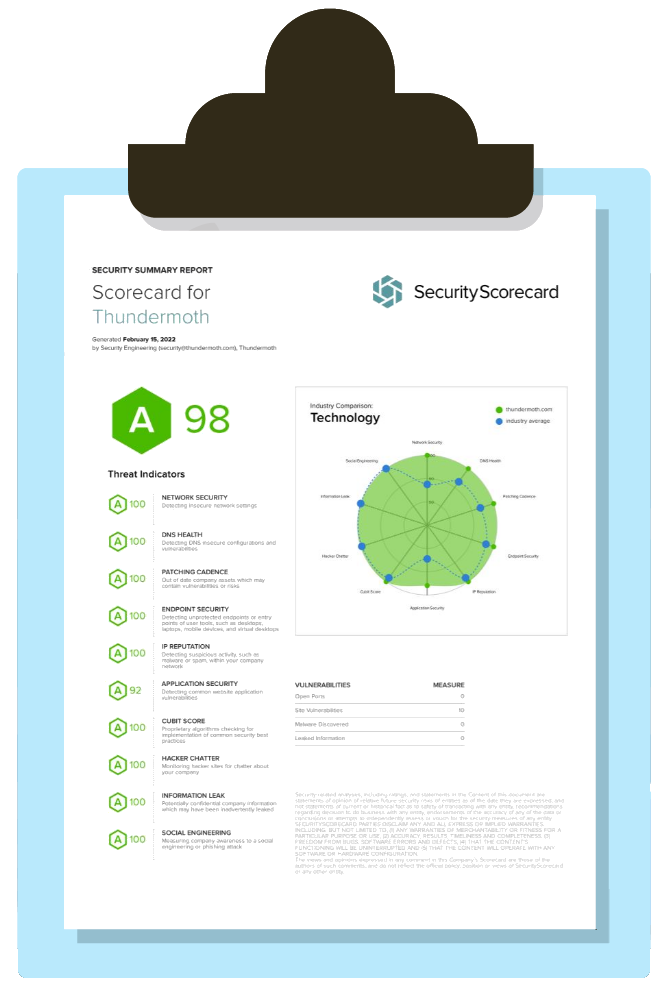
Security Practices
Thundermoth is founded on security. Both our software and internal security posture are built on adhering to CIS guidelines. We conduct routine internal and external security audits and penetration tests.
View Security Scorecard


Cloud Security Stack
Our layered cloud security stack offers the latest security protections within the cloud.